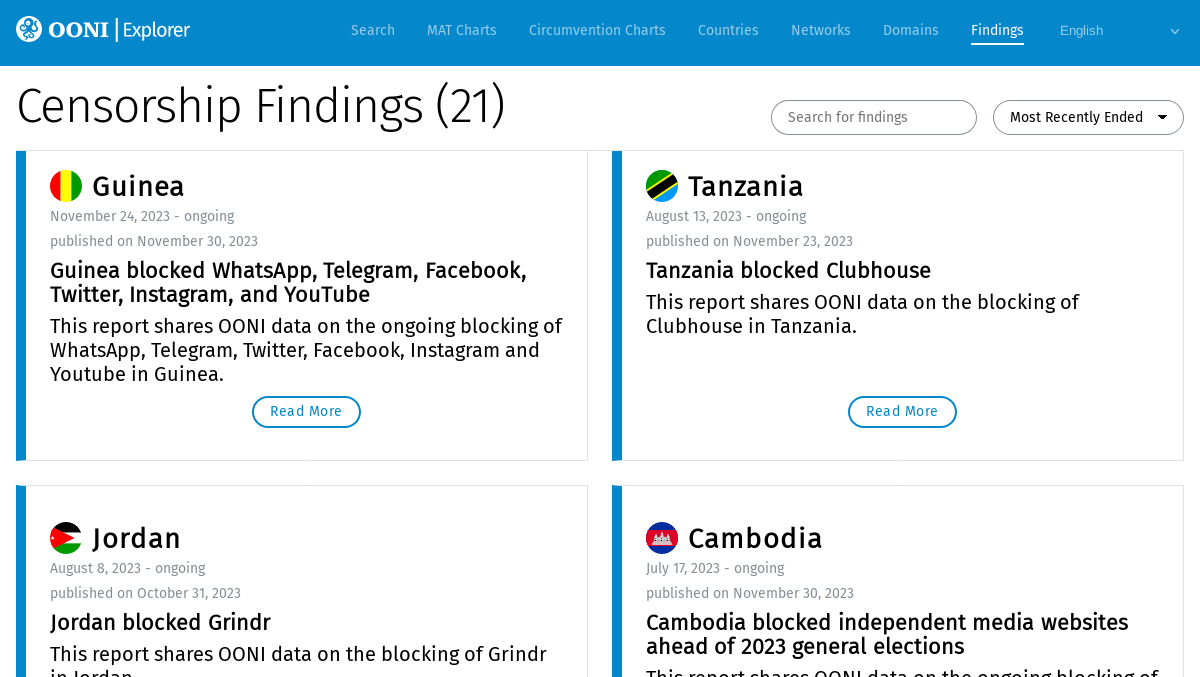
Some documented Internet censorship events in 2023
CS3640

How might a middlebox detect that a client is trying to access a prohibited destination and/or prohibited information?
How might a middlebox detect that a client is trying to access a prohibited destination and/or prohibited information?
Having detected something it wants to prevent, how might a middlebox block a connection?
$ dig dw.com
C:\> nslookup dw.com
$ dig dw.com ; <<>> DiG 9.16.44-Debian <<>> @1.1.1.1 dw.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23145 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;dw.com. IN A ;; ANSWER SECTION: dw.com. 164 IN A 194.55.30.46 dw.com. 164 IN A 194.55.26.46 ;; Query time: 3 msec ;; SERVER: 1.1.1.1#53(1.1.1.1) ;; WHEN: Thu Dec 07 03:45:39 UTC 2023 ;; MSG SIZE rcvd: 67
95.85.120.6 is the IP address of a host located in Turkmenistan.
(It's not a DNS server though!)
What happens when you send a DNS query through the firewall hosts that surround Turkmenistan's network?
$ dig @95.85.120.6 dw.com
C:\> nslookup dw.com 95.85.120.6
$ dig @95.85.120.6 dw.com ; <<>> DiG 9.16.44-Debian <<>> @95.85.120.6 dw.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 22268 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;dw.com. IN A ;; ANSWER SECTION: dw.com. 300 IN A 127.0.0.1 ;; Query time: 246 msec ;; SERVER: 95.85.120.6#53(95.85.120.6) ;; WHEN: Thu Dec 07 03:48:15 UTC 2023 ;; MSG SIZE rcvd: 40
Reference: Measuring and Evading Turkmenistan's Internet Censorship 2023.
159.226.244.24 is the IP address of a host located in China. (Also not a DNS server.)
$ dig @159.226.244.24 dw.com
C:\> nslookup dw.com 159.226.244.24
$ dig +short @159.226.244.24 dw.com 75.126.164.178 $ dig +short @159.226.244.24 dw.com 67.15.129.210 $ dig +short @159.226.244.24 dw.com 128.121.146.101 $ dig +short @159.226.244.24 dw.com 31.13.95.34 $ dig +short @159.226.244.24 dw.com 69.63.181.12 $ dig +short @159.226.244.24 dw.com 168.143.162.58
Reference: How Great is the Great Firewall? Measuring China's DNS Censorship.
How does providing a fake DNS response prevent a user from accessing a domain?
The DNS injection systems in Turkmenistan and China are bidirectional, meaning they don't make a distinction between inbound and outbound packets.
(Remote censorship measurement systems like Censored Planet take advantage of this and other properties, to measure levels of censorship without needing a physical presence in another country.)
Not all forms of censorship are this easy to test and see.
What can a client do to circumvent a block of some desired destination/information?
ssh -D server)All-in-one systems:
The censor can use the system too, and study how it works.
What prevents a censor from discovering all your proxy IP addresses and blocking them?
The key question is:
What does it cost a censor to block the system?
Protocol obfuscation is not enough.
You need to somehow protect the endpoints too.
https://github.com/net4people/bbs, a censorship circumvention forum that I manage.
https://ntc.party/, another active forum.
https://snowflake.torproject.org/, run a browser extension to help people circumvent censorship.
https://ooni.org/, install an app to measure censorship.
David Fifield