Threat modeling and circumvention
of Internet censorship
David Fifield
The “border firewall”
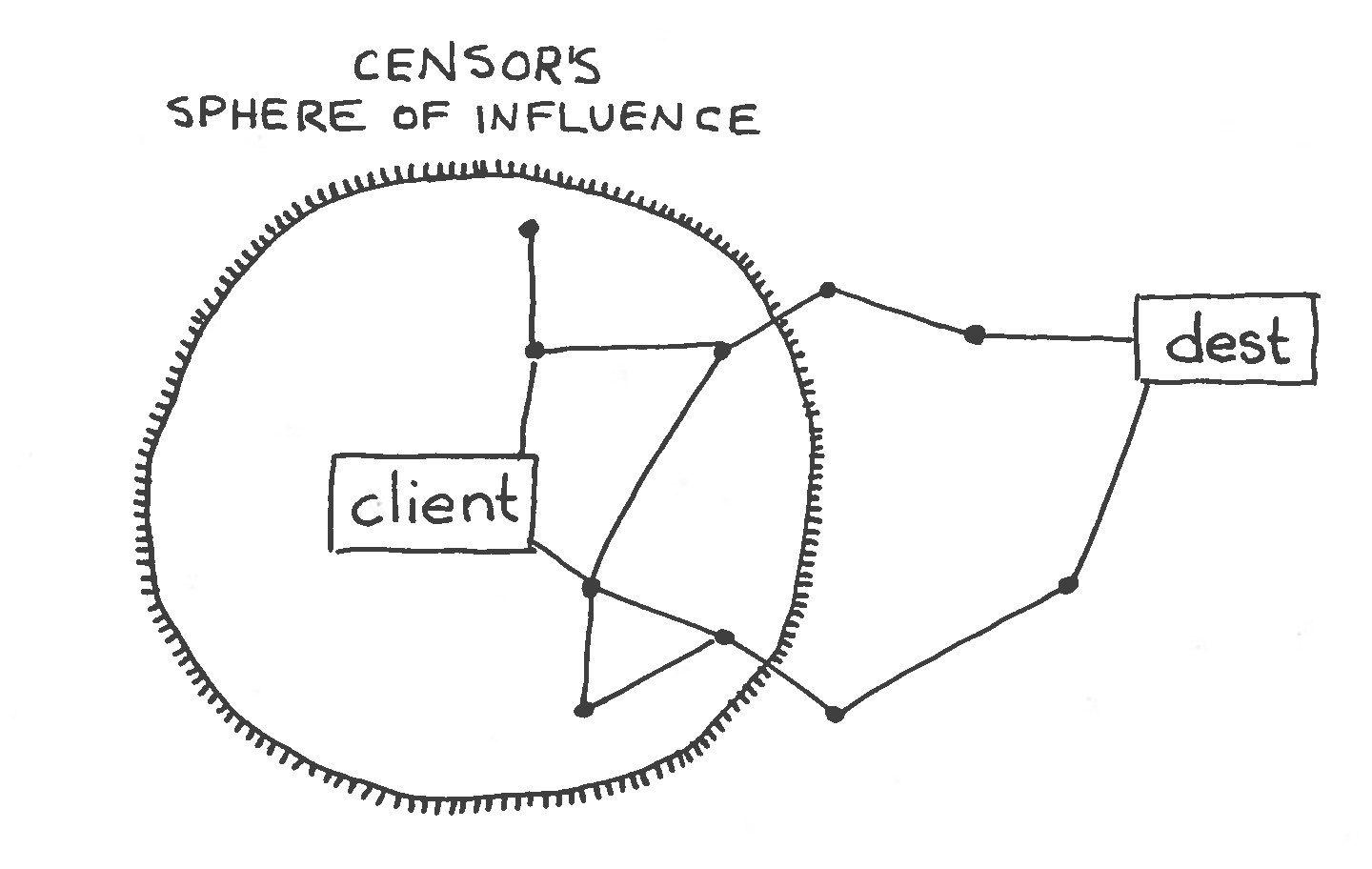
Circumvention is reaching the destination
despite the censor’s controls.
Commonly assumed
censor capabilities
- IP/port blocking
- control of specific DNS servers
- packet injection (of DNS responses, TCP resets)
- keyword filtering
- protocol parsing (deep packet inspection)
Sometimes:
- throttling
- packet dropping
- (temporary) shutdowns
Does it make sense to design against the strongest imaginable censor?
Collateral damage
Accidental blocking by the censor,
incurred in the course of trying to block
something else.
Collateral damage
Accidental blocking by the censor,
incurred in the course of trying to block
something else.
According to the usual threat models,
collateral damage is the only tool
the circumventor has.
Virtually all circumvention systems
can be understood in terms of collateral damage.
Circumvention systems
Circumvention needs to disguise both
address and content.
Disguising content can be steganographic
(“look like something”) or randomized
(“look like nothing”).
Disguising an address requires protecting the destination
and any proxy servers.
- careful proxy distribution (BridgeDB)
- quickly changing proxies (flash proxy, Snowflake)
- cooperating middle nodes (decoy routing, domain fronting)
My research topics
- Building circumvention systems according to evolving censor models
- Empirically testing real-world censors to generate better models
- Evaluating existing circumvention systems against realistic models
1. Building circumvention systems
-
Flash proxy (retired)
“Evading Censorship with Browser-Based Proxies,”
by David Fifield, Nate Hardison, Jonathan Ellithorpe, Emily Stark, Roger Dingledine, Phil Porras, and Dan Boneh.
-
OSS (never deployed)
“OSS: Using Online Scanning Services for Censorship Circumvention,”
by David Fifield, Gabi Nakibly, and Dan Boneh.
-
Domain fronting (now in use)
“Blocking-resistant communication through domain fronting,”
by David Fifield, Chang Lan, Rod Hynes, Percy Wegmann, and Vern Paxson.
-
Snowflake (under development)
Arlo Breault, David Fifield, and Serene Han.
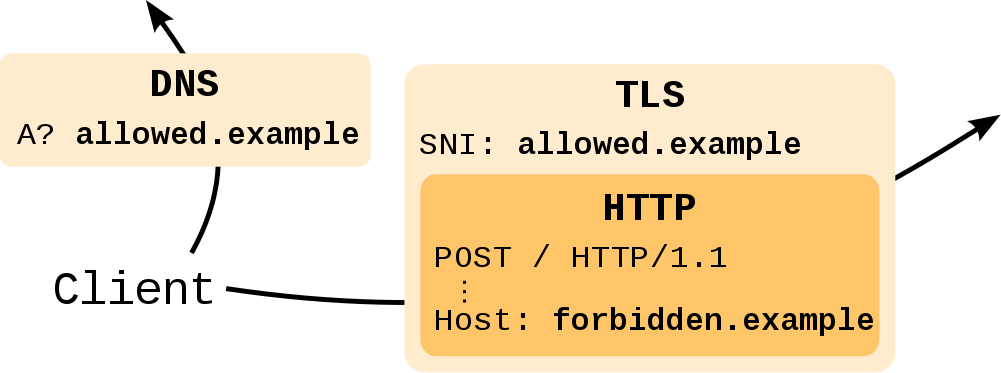
2. Testing real-world censors
-
Active probing by the firewall in China
“Examining How the Great Firewall Discovers Hidden Circumvention Servers,”
by Roya Ensafi, David Fifield, Philipp Winter, Nick Feamster, Nicholas Weaver, and Vern Paxson.
-
Censor reaction time
“Censors’ Delay in Blocking Circumvention Proxies,”
by David Fifield and Lynn Tsai.
Ongoing research with Lynn Tsai and Qi Zhong.
“We think of censors as complex systems,
consisting of interacting human and machine
components, whose goals and
motivations are sometimes in conflict.”
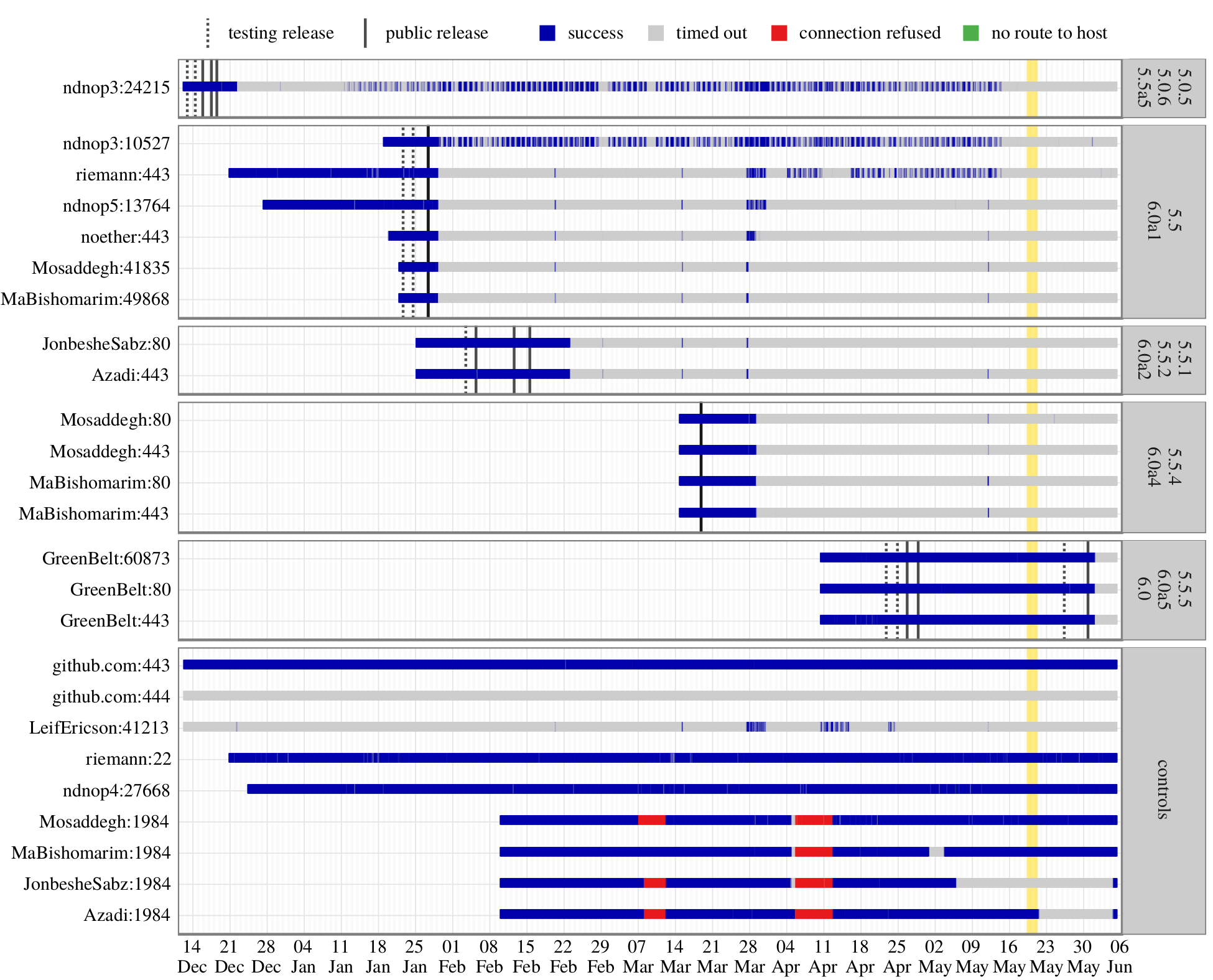
3. Evaluating circumvention systems against models
-
How circumvention is evaluated
“Towards Grounding Censorship Circumvention in Empiricism,”
by Michael Carl Tschantz, Sadia Afroz, Anonymous, and Vern Paxson.
“We assess both deployed circumvention approaches and research
proposals to consider the criteria employed in their evaluations
and compare these to the observed behaviors of
real censors, identifying areas where
evaluations could more faithfully and effectively incorporate
the practices of modern censors.”
My remaining research time will be spent on
completing a study of censors’ reaction times;
and in deploying Snowflake and documenting its effects.



